Permissions on Non-default Column Families
If
a JSON document field is not in the HPE Ezmeral Data Fabric Database JSON default column
family, you must have readperm and writeperm permissions to
perform read and write operations on the field. To mask data fields, you
must have the defaultunmaskedreadperm or the
unmaskedreadperm permission. You either receive the permissions from
the column family, inherit them from the field's parent field, or have the permissions from an
explicit grant on the field.
The following diagram shows a JSON document where fields b and
c are in a column family cf1 that is defined at field
b with the path a.b.
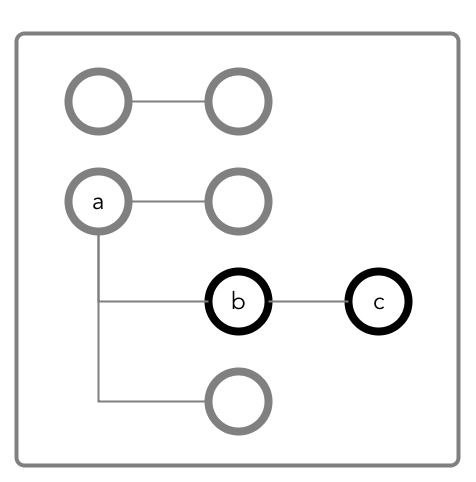
Granting Read and Write Permissions on Field c
To perform both read and write operations on field c, when it is in column
family cf1, you must have both readperm and
writeperm access on field c:
- If you have
readpermandwritepermpermissions oncf1, then you have access to fieldc. - If you have
readpermandwritepermpermissions on fieldb, then you have access to fieldc. You do not need any further permissions. Fieldcinherits yourreadpermandwritepermpermissions from fieldb. - If you have
readpermandwritepermpermissions oncf1but either fieldaorbdenied you permissions:- You must have
traversepermpermission granted to you on the field that denied you access (fieldaorb). - You must have
readpermandwritepermpermissions explicitly granted to you on fieldc.
- You must have
- If you do not have
readpermandwritepermpermissions oncf1:- You must have
traversepermpermission granted to you on eithercf1or field b. - You must have
readpermandwritepermpermissions explicitly granted to you on fieldc.
- You must have
The following are examples of commands that grant these permissions:
/opt/mapr/bin/maprcli table cf colperm set
-path <path to JSON table >
-cfname cf1
-name a.b
-traverseperm u:<user ID> | <existing ACE for this field> /opt/mapr/bin/maprcli table cf colperm set
-path <path to JSON table >
-cfname cf1
-name a.b.c
-readperm u:<user ID> | <existing ACE for this field>
-writeperm u:<user ID> | <existing ACE for this field>/opt/mapr/bin/maprcli table cf edit
-path <path to JSON table >
-cfname cf1
-traverseperm u:<user ID> | <existing ACE for this field> /opt/mapr/bin/maprcli table cf colperm set
-path <path to JSON table >
-cfname cf1
-name a.b.c
-readperm u:<user ID> | <existing ACE for this field>
-writeperm u:<user ID> | <existing ACE for this field> Granting Read or Write Permission on Field c
To perform either read or write operations on field c, when it is in
column family cf1, you must have either readperm or
writeperm access on field c:
- If you have the same permission (
readpermorwriteperm) oncf1, then you have access to fieldc. - If you have the same permission (
readpermorwriteperm) on fieldb, then you have access to fieldc. You do not need any further permissions. Fieldcinherits yourreadpermorwritepermpermission from fieldb. - If you have the same permission (
readpermorwriteperm) oncf1but either fieldaorbdenied you permission:- You must have
traversepermpermission granted to you on the field that denied you access (fieldaorb). - You must have
readpermorwritepermpermission explicitly granted to you on fieldc.
- You must have
- If you do not have the same permission (
readpermorwriteperm) oncf1:- You must have the
traversepermpermission granted to you on eithercf1or fieldb. - You must have
readpermorwritepermpermission explicitly granted to you on fieldc.
- You must have the
The following example grants traverseperm permission:
/opt/mapr/bin/maprcli table cf colperm set
-path <path to JSON table>
-cfname cf1
-name a.b
-traverseperm u:<user ID> | <existing ACE for this field> The following example grants readperm permission:
/opt/mapr/bin/maprcli table cf colperm set
-path <path to JSON table>
-cfname cf1
-name a.b.c
-readperm u:<user ID> | <existing ACE for this field>Permissions for Dynamic Data Masking
In addition to the existing readperm, writeperm and
traverseperm database permissions, there are two new database permissions
to support Dynamic Data Masking:
-
The
defaultunmaskedreadpermpermission, when set at the table level, applies to all column families within that table unless otherwise overridden by theunmaskedreadpermsetting at the CF or column level. -
The
unmaskedreadpermpermission, when applied at the CF or column level, specifies the users who can retrieve unmasked values for the specified database column. Users with regularreadpermprivileges but withoutunmaskedreadpermprivileges will only be able to view the masked data. This permission is only applicable to columns that have the dynamic data mask attribute set. Specifying this permission on an unmasked column will have no effect.
mapr can read column
Creditcard from the default CF of table /table1
unmasked. User user1 can read the Creditcard column, but
it will be masked:
maprcli table cf colperm set -path /table1 -cfname default \
-name Creditcard -readperm "u:user1|u:mapr" -unmaskedreadperm "u:mapr" \
-writeperm "u:mapr"
maprcli table cf column securitypolicy set -path /table1 -cfname default \
-name Creditcard -securitypolicy pci
maprcli table cf column datamask set -path /table1 -cfname default \
-name Creditcard -datamask mrddm_last4
maprcli table cf column list -path /table1 -cfname default -json
{
"timestamp":1612303576139,
"timeofday":"2021-02-02 02:06:16.139 GMT-0800 PM",
"status":"OK",
"total":1,
"data":[
{
"name":"Creditcard",
"aces": {
"readperm":"u:user1|u:mapr",
"unmaskedreadperm":"u:mapr",
"writeperm":"u:mapr"
},
"securitypolicy":"pci",
"datamask":"mrddm_last4"
}
]
}