Obtaining readperm or writeperm on
Fields
In this scenario, you want to perform an operation on a field, and the operation requires that you have readperm or writeperm permissions on that field. How you obtain either permission depends on whether the field is in the default column family or a non-default column family.
If the field is in the default column family
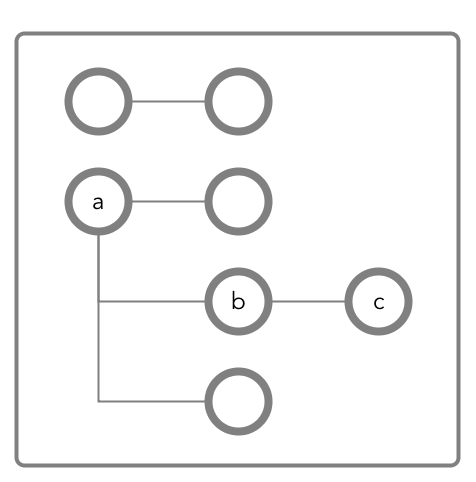
In the following document, you want to perform an operation on field c,
which is in the default column family. The operation requires you to have
readperm or writeperm on field c.
- Case 1: You have the same permission (
readpermorwriteperm) on the default column family - In this case, field
cinherits the permission, assuming that the permission was not denied on fieldaorb.If you do not have
readpermorwritepermon fieldaorb, you needtraversepermon the field that denied you the permission that you need. You also needreadpermorwritepermexplicitly granted to you on fieldc.Example commands to grant these permissions:
/opt/mapr/bin/maprcli table cf colperm set -path <path to JSON table> -cfname default -name a.b -traverseperm u:<user ID> | <existing ACE for this field>The next example command grants
readperm:/opt/mapr/bin/maprcli table cf colperm set -path <path to JSON table> -cfname default -name a.b.c -readperm u:<user ID> | <existing ACE for this field> - Case 2: You do not have the same permission (
readpermorwriteperm) on the default column family - In this case, you need the
traversepermpermission on the default column family. You also needreadpermorwritepermexplicitly granted to you on fieldc.Example commands to grant these permissions:
/opt/mapr/bin/maprcli table cf edit -path <path to JSON table> -cfname cf1 -traverseperm u:<user ID> | <existing ACE for this field>This next example command grants
readperm:/opt/mapr/bin/maprcli table cf colperm set -path <path to JSON table> -cfname cf1 -name a.b.c -readperm u:<user ID> | <existing ACE for this field>
If the field is in a non-default column family
In the following document, you want to perform an operation on field c,
which is in the column family that is defined at field b with the path
a.b. The operation requires you to have readperm or
writeperm on field c.
b and
c are in a column family that has the path a.b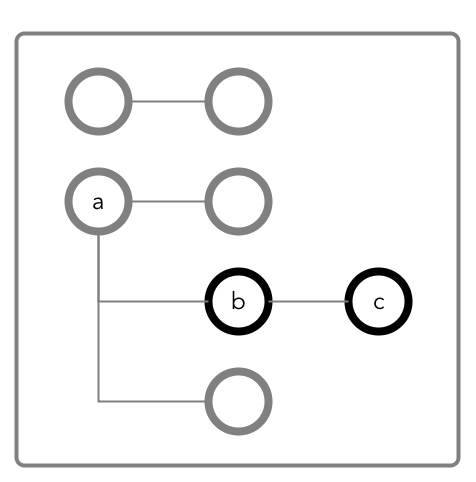
- Case 1: You do not have the permission you need (
readpermorwriteperm) on fieldb - You need
traversepermon fieldb, and you needreadpermorwritepermgranted to you explicitly on fieldc.Example commands to grant these permissions:
/opt/mapr/bin/maprcli table cf edit -path <path to JSON table> -cfname cf1 -traverseperm u:<user ID> | <existing ACE for this field> maprcli table cf colperm set -path <path to JSON table> -cfname cf1 -name a.b.c -readperm u:<user ID> | <existing ACE for this field> - Case 2: You do have the permission you need (
readpermorwriteperm) on fieldb - You do not need any further permissions. Field
cinherits yourreadpermandwritepermpermissions from fieldb.