About Access and Refresh Tokens
Describes how to use the downloadable tokens provided for client access.
How Clients Use Tokens
In Data Fabric deployments where SSO is configured, you must provide an SSO user name and password for access to a fabric. Clients that aren’t aware of SSO user names and passwords can gain access to RPC communications by using JSON web tokens (JWTs). A JSON Web Token (JWT) is a method for securely transmitting information between services in a computing system.
maprclihadoopmcfuse(service start)loopback nfs(service start)
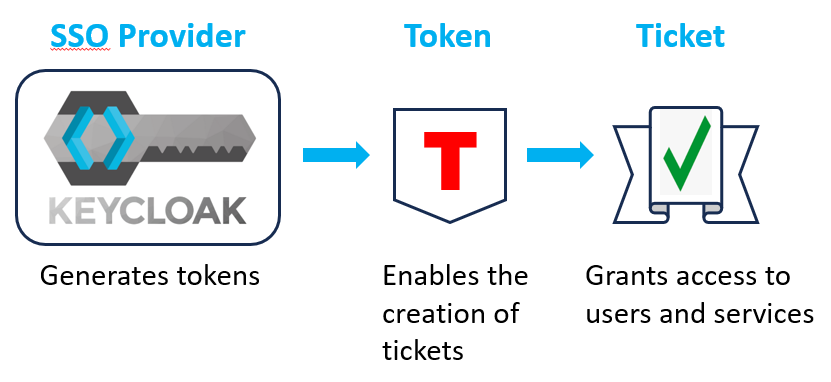
The ticket allows the command line to connect to the CLDB service. To facilitate the process, you must obtain a token from the SSO provider and place it in a secure location that can be specified in an environment variable. Exporting the environment variable creates a temporary ticket, enabling the CLI to talk to the CLDB server. This method permits the use of any command without a password for the duration of the ticket.
For more information about Data Fabric tickets, see Managing Tickets.
Downloading the Tokens
jwt_tokens.tar.gz file, which are extracted to the client. The
jwt_tokens.tar.gz file contains the following token files:| Token Type | File | Function |
|---|---|---|
| Access | jwt_access |
Encapsulates the user's authentication information within the fabric. |
| Refresh | jwt_refresh |
Enables the creation of a new access token when the current access token expires. |
For more information about downloading the tokens, see Installing Client Libraries.
Exporting the Tokens
| Client | To export the tokens . . . |
|---|---|
| Hadoop | Use these
commands: |
| Fuse POSIX | Add the export paths shown for the Hadoop client in the first row of this
table to the top of the following file:
|
| Loopback NFS | Add the export paths shown for the Hadoop client in the first row of this
table to the top of the following file:
|
core-site.xml file.
Adding them to core-site.xml file causes the fabric to use the designated
tokens every time you log on. To add the tokens, specify the following property in
the core-site.xml:<property>
<name>fs.mapr.sso.tokenpath</name>
<value>/root/jwt_access</value>
</property>Token and Ticket Expiration and Renewal
Tokens and tickets expire after a short time. By default, Keycloak-generated tokens expire after two (2) hours. Short-lived tickets expire after 20 minutes.
If an access token expires or becomes invalid, the client application can use a refresh token to obtain a new access token without requiring the user to re-authenticate. The client application sends Keycloak a token-refresh request along with the current refresh token. Keycloak validates the refresh token and issues a new access token. This automatic-refresh mechanism repeats itself to allow client jobs to run for days or weeks as long as the tokens remain valid.
Changing Token and Ticket Durations
To check or change the expiry setting for short-lived tickets, see Checking and Changing the Temporary Ticket Duration.
To change the expiration setting for a token, you must be the fabric manager and have access to the Keycloak UI.
Access Token Expiry
- Log in to the Keycloak admin console. See Accessing the Keycloak Administration Console.
- Select the realm for which you want to configure the access token expiry time.
- Go to the Realm Settings > Tokens tab.
- In the Access Token Lifespan field, specify the desired expiration time for the access tokens in hours, minutes, or days.
- Save your changes.
Refresh Token Expiry
- Log in to the Keycloak admin console. See Accessing the Keycloak Administration Console.
- Select the realm for which you want to configure the access token expiry time.
- Go to the Realm Settings > Sessions tab.
- In the SSO Session Max field, specify the desired maximum lifespan for refresh tokens in minutes, hours, or days.
- Save your changes.