Add, edit, delete, and manage state of security policies.
A security policy is an access control mechanism that can be applied to data objects
on a fabric. Once a security policy is applied, it governs how a user can access
data objects on the volume to which the security policy is applied.
A security policy can be associated with a volume.
Security Policy Life Cycle
The state of a security policy is interpreted as a combination of two parameters:
- allow tagging
- access control
The following table explains the various values of the allow tagging and access
control parameters.
| Parameter |
Accepted Values and Description |
Default value |
| allow tagging |
false
- Disables tagging; users cannot apply the security policy
to data objects.
- This is the default setting when the fabric manager
creates a security policy. The fabric manager can
specify the setting explicitly when creating the
security policy.
- When a security policy is active (allow tagging=true)
but needs to be deprecated, modify the policy and set
allow tagging=false. This prevents users from tagging
any other data objects with the policy. Note that the
system continues to enforce the security controls set in
the security policy for data objects that were already
tagged with the security policy.
true
- Enables tagging; users can apply the security policy
to data objects.
- When creating or modifying a security policy, a
fabric manager can set allowtagging to true.
- When creating a security policy, as a fabric
manager, you may want to set this parameter to true
to test the security settings in the policy or to
use tagging tools to discover data content and tag
the data.
- To enable a deprecated security policy, set allow
tagging to true.
|
false |
| access control |
Disarmed
- Unless the fabric manager changes the setting when
creating the security policy, this is the default
setting if the fabric manager creates a security
policy.
- The system does not enforce the access permissions set
in the security policy during data operations on the
data objects tagged with the security policy.
Armed
-
The system enforces the permissions set in the
security policy during data operations on the data
objects tagged with the security policy.
-
When creating or modifying a security policy, as a
fabric manager, you can set access control to
Armed.
- To enforce access permissions set in a deprecated
security policy, the fabric manager can set access
control to Armed. The system continues to enforce
access permissions set in the security policy for all
data operations on the data objects tagged with the
policy.
Denied
- Denies all access to data objects tagged with the
security policy.
|
Disarmed |
You can change the state of a security policy through the allow
tagging and access control parameters to move a
security policy through a life cycle, as shown in the following image where the
security policy moves from new to retired.
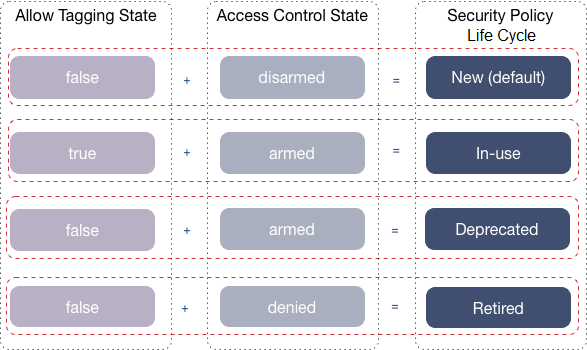
The following table describes each of the stages in the security policy life
cycle:
| Stage |
Description |
| new (default) |
- Default upon security policy creation.
- Users cannot tag data objects with the security
policy.
- The system does not enforce access permissions set in
the security policy
|
| in use |
- Users can tag data objects with the security
policy.
- The system enforces all security controls set in the
security policy during data operations on data objects
tagged with the security policy.
- Security controls set in the policy can include access
permissions, auditing, and wire-level encryption.
|
| deprecated |
- Users can no longer tag the security policy to data
objects.
- The system still enforces the security controls set in
the security policy for all data operations on the data
objects tagged with the policy. Users cannot tag any
additional data objects with the policy.
|
| retired |
- Users cannot tag the security policy to data
objects.
- All data operations on the data objects tagged with the
security policy are denied by the system.
|
