Configuring SSO
Describes how the HPE Ezmeral Data Fabric supports single sign-on (SSO) and how to configure it.
HPE Ezmeral Data Fabric releases 7.3.0 and later support SSO when configured with the Keycloak identity and access management (IAM) solution. No other IAM solution is currently supported.
Configuring SSO is optional. If you do not configure SSO, you must use Data Fabric user names and passwords for access to the cluster. While SSO is supported for Data Fabric core, it is not supported for the Installer or ecosystem components.
Keycloak Is Preinstalled and Preconfigured
Keycloak is the
identity and access management (IAM) solution that provides single-sign-on (SSO) support
for the Data Fabric. Starting with release 7.5.0,
Keycloak is preinstalled and preconfigured when you install the
mapr-keycloak package and specify the -keycloak
option in configure.sh as part of cluster
creation.
| Keycloak Preconfigured Items | How Many? | Names | Notes |
|---|---|---|---|
| Users | 1 | admin |
Any additional users that are added must be created with
uid and gid attributes, as described
in Adding New Users to Keycloak. |
| Groups | 1 | fabric-manager |
Any additional groups that are added must be created with the
gidNumber attribute, as described in Adding a Group to Keycloak. |
| Roles | 3 | fabric-manager
|
These are the only supported roles. The developer
role is sometimes referred to as the "fabric user" role. |
| Clients | 1 | edf-client |
This is the dedicated client for the Data Fabric. In Keycloak, a client is an application or service that can request authentication for a user. |
SSO and Temporary Tickets
Enhancements in release 7.3.0 and later allow clients that aren’t aware of user passwords to access the cluster if they have a valid token from an SSO provider.
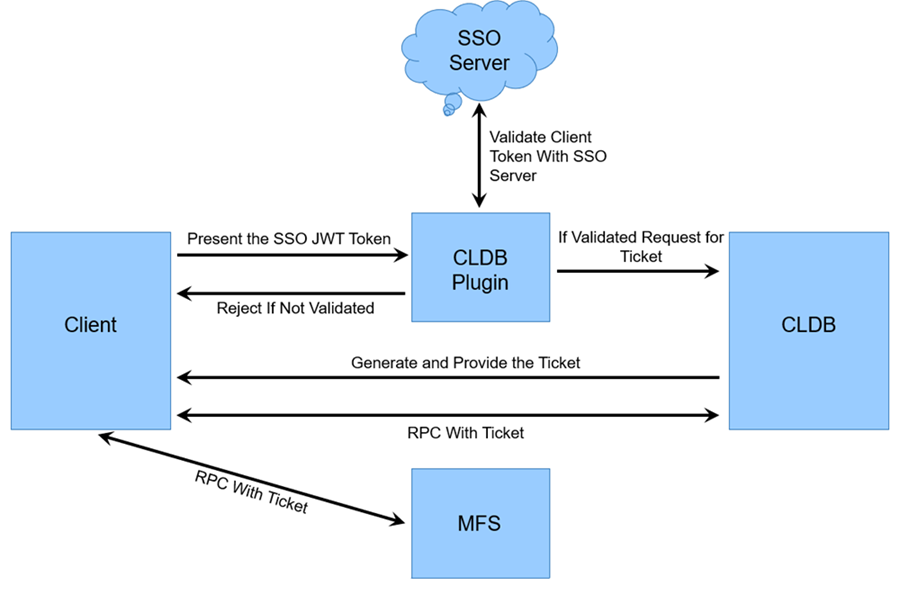
In Data Fabric installations that are not configured for SSO, users authenticate by providing a username and password and must obtain a user ticket to issue commands. The ticket enables RPC communication between various Data Fabric services. RPC communication cannot occur without a ticket.
Beginning with release 7.3.0, in installations where SSO is configured, a user provides a password to an SSO provider. The SSO provider authenticates the user and provides a JSON web token (JWT). The client presents the JWT to the CLDB using HTTPS. A CLDB plugin (new in release 7.3.0) functions as an HTTPS server and validates the JWT from the SSO provider. If the token is valid, the CLDB provides a short-lived ticket to the client.
Object Store and Temporary Tickets
Releases 7.3.0 and later also provide enhancements to enable MinIO Client (mc)
communication with the HPE Ezmeral Data Fabric Object Store by using temporary tickets. In non-SSO
installations, users and applications authenticate to the Object Store through S3 keys
(AccessKey and SecretKey). Release 7.3.0 extended the MC framework to use
maprcli with JWT to obtain a temporary AccessKey and SecretKey in
the background. Optimizations in the CLDB allow the CLDB to cache the AccessKey and
SecretKey for 15 minutes.