Using LDAP Mappers
Describes how to use mappers to auto-populate Keycloak with the mandatory attributes it needs for users and groups to access the Data Fabric UI.
If you integrated your LDAP Directory with Keycloak as described in Integrating Your LDAP Directory with Keycloak, you must configure mappers to
associate Keycloak user, role, and group attributes with your LDAP users. Three
mappers need to be created:
- UID mapper
- GID mapper
- User group mapper
Creating the UID Mapper
To create the UID mapper:
- Sign in to the Keycloak administration console as described in Accessing the Keycloak Administration Console. The master realm information is displayed:
- In the left-navigation pane, click User federation. The User federation screen appears.
- Click the box for the LDAP provider that you configured in Integrating Your LDAP Directory with Keycloak. The LDAP screen appears.
- Click the Mappers tab to display the current list of mappers.
- To add a mapper, click Add mapper. The Create new mapper screen appears.
- Specify a name for the UID mapper. The following example uses the name
uidjim: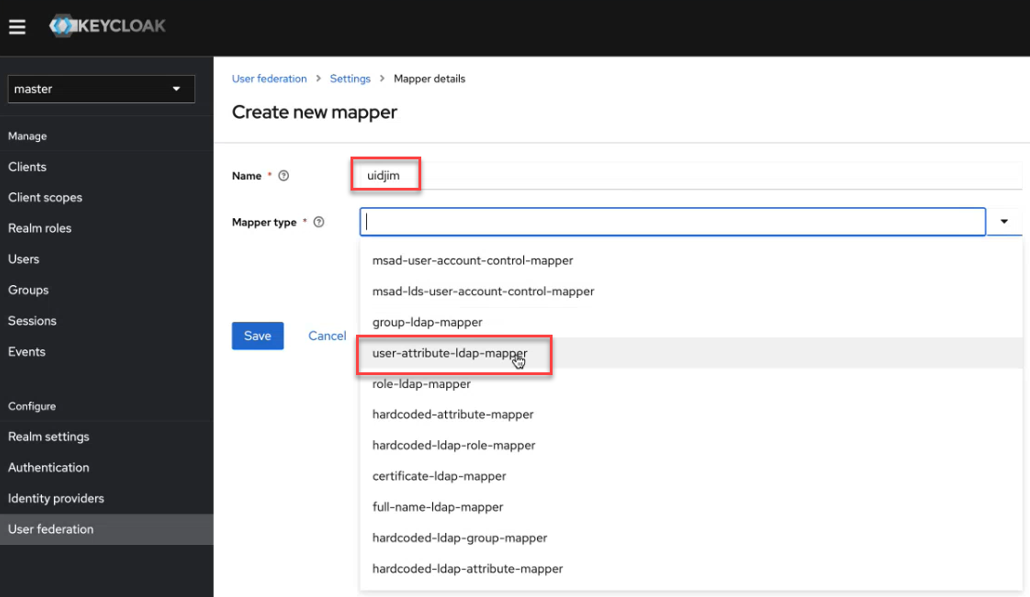
- In the Mapper type field, click the down arrow, and select
user-attribute-ldap-mapper. The Mapper details screen appears. - Fill out the UID mapper as follows:
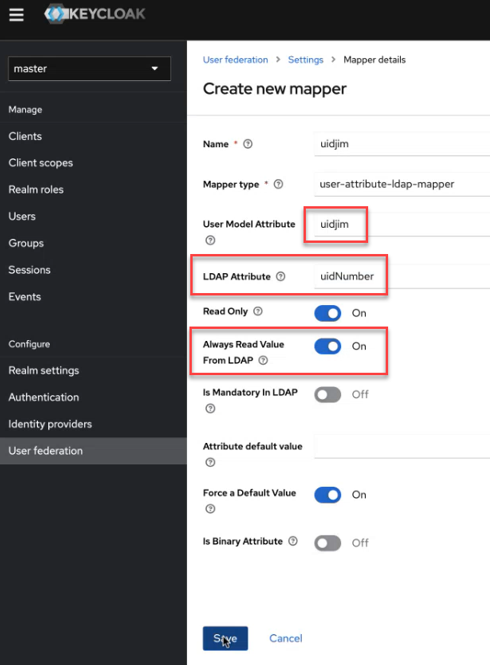
- Click Save.
Creating the GID Mapper
To create the GID mapper:
- Sign in to the Keycloak administration console as described in Accessing the Keycloak Administration Console. The master realm information is displayed:
- In the left-navigation pane, click User federation. The User federation screen appears.
- Click the box for the LDAP provider that you configured in Integrating Your LDAP Directory with Keycloak. The LDAP screen appears.
- Click the Mappers tab to display the current list of mappers.
- To add a mapper, click Add mapper. The Create new mapper screen appears.
- Specify a name for the GID mapper.
- In the Mapper type field, click the down arrow, and select
user-attribute-ldap-mapper. The Mapper details screen appears. - Fill out the UID mapper as follows:
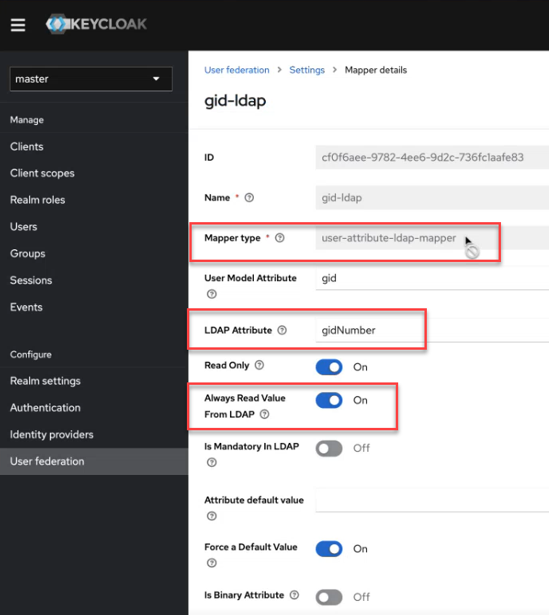
- Click Save.
Creating the User Group Mapper
To create the User Group mapper:
- Sign in to the Keycloak administration console as described in Accessing the Keycloak Administration Console. The master realm information is displayed:
- In the left-navigation pane, click Clients. The Clients list tab appears.
- Click the edf-client entry.
- In the right pane, click the Client scopes tab.
- Click the edf-client-dedicated entry.
- Click Add mapper > By configuration. The
Configure a new mapper screen appears:
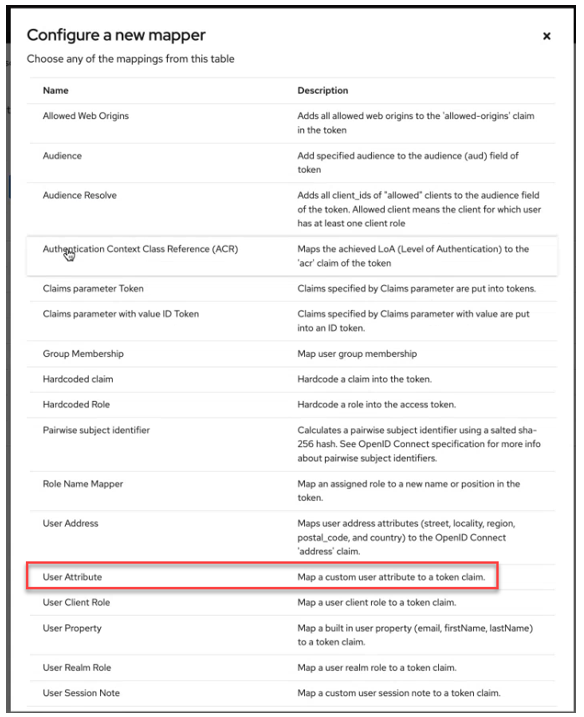
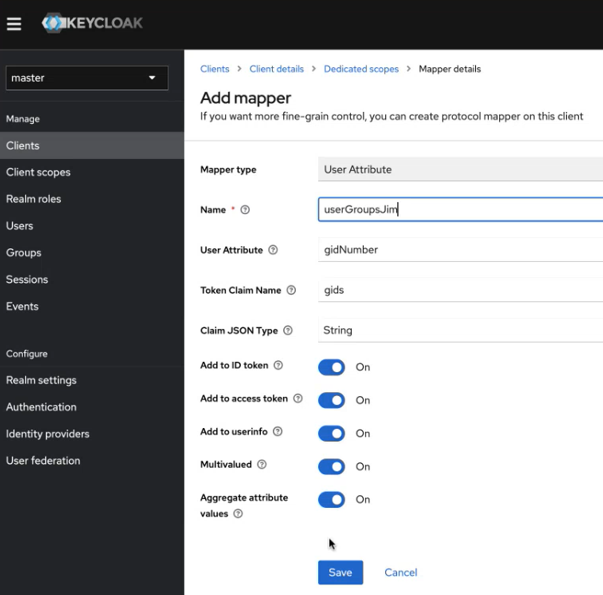
- Click the User Attribute row. Selecting this row allows you to map a custom attribute to a token claim. The Add mapper screen appears.
- Fill out the form like this, using a name that is appropriate for your
installation:
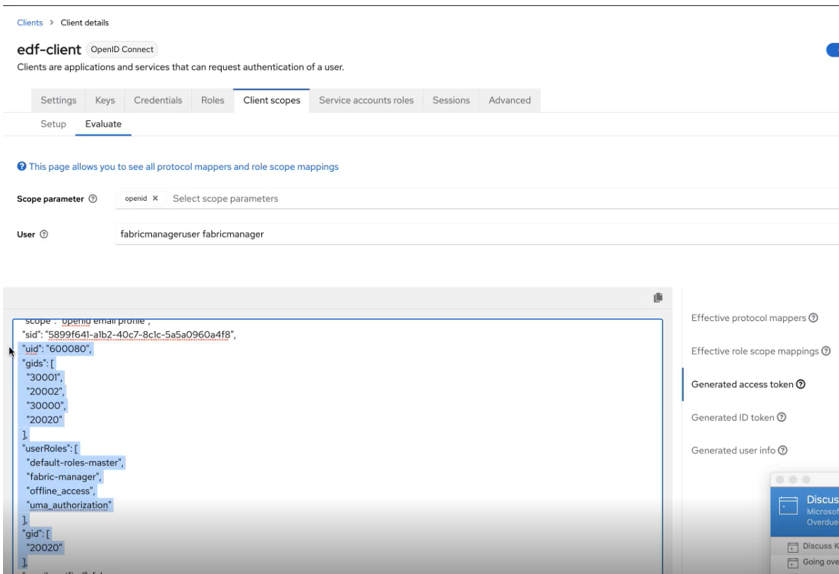
Confirming that Required Attributes Are Part of the JWT Token for a User
To confirm the required attributes:
- Sign in to the Keycloak administration console as described in Accessing the Keycloak Administration Console. The master realm information is displayed:
- In the left-navigation pane, click Clients. The Clients list tab appears.
- Click the edf-client entry.
- In the right pane, click the Client scopes tab.
- Click Evaluate.
- In the User field, type the name of a user. For example,
type the name of the fabric manager user:
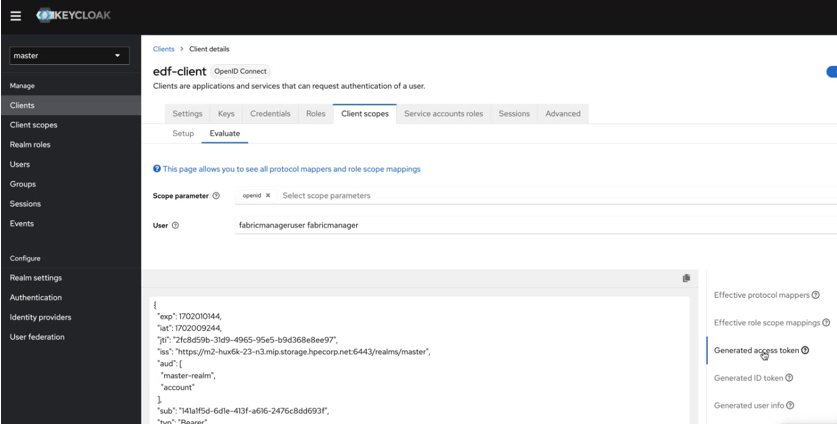
- Scroll down to check that the following four items are populated in the JWT
token. If any of them are missing, there might be issues with user
permissions: