Plain Authentication
An administrator can configure Drill to use the Linux pluggable authentication module (PAM) for Plain (username and password) authentication. PAM provides an authentication module that interfaces with any installed PAM authentication entity, such as the local operating system password file (/etc/passwd) or LDAP.
When using PAM for authentication, each user with permission to run Drill queries must exist in the list of users that resides on each Drill node in the cluster. The username (including uid) and password for each user must be identical across all Drill nodes.
Authentication Process Overview
During the authentication process, the client passes a username and password to the Drillbit as part of the connection request, which then passes the credentials to PAM. If PAM authenticates the user, the connection request passes the authentication phase, and the connection is established. The user will be authorized to access Drill and issue queries against the filesystem or other storage plugins, such as Hive.
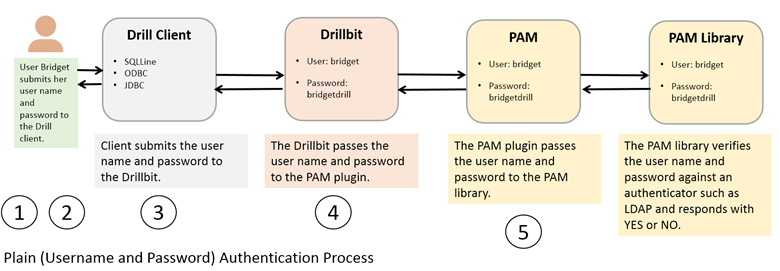
If PAM cannot authenticate the user, the connection request does not pass the authentication phase and the user will not be authorized to access Drill. The connection is terminated as AUTH_FAILED.
For more PAM information (including a JPAM User Guide), see JPAM.
Configuring Plain Authentication in Drill
The following sections provide information for configuring Drill to use libpam4j or libjpam, as well as instructions for connecting to Drill from SQLLine and BI tools when Plain authentication is enabled: