User Impersonation
Impersonation allows a service to act on behalf of a client while performing the action
requested by the client. By default, user impersonation is disabled in Drill. You can configure
user impersonation in the
/opt/mapr/drill/drill-<version>/drill-override.conf file.
When you enable impersonation, Drill executes all the client requests as the user logged in to the client. Drill passes the user credentials to the file system, and the file system checks to see if the user has permission to access the data. When you enable authentication, Drill uses the pluggable authentication module (PAM) to authenticate a user’s identity before the user can access the Drillbit process.
If impersonation is disabled, Drill executes all of the client requests against the file system as the user that started the Drillbit service on the node. This is typically a privileged user. The file system verifies that the system user has permission to access the data.
User Impersonation Example
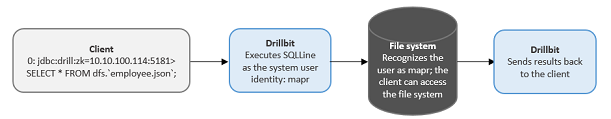
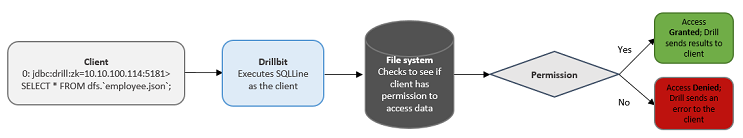
Impersonation Support
- Clients
- ODBC
- JDBC
- REST API
- Drill Web UI
- Storage plugins
- file system
- HPE Ezmeral Data Fabric Database
- Hive
- Types of queriesDrill applies impersonation to queries issued using the following commands:NOTEWhen you enable impersonation, the setting applies to queries on data and metadata. For example, if you issue the SHOW SCHEMAS command, Drill impersonates the user logged into the client to access the requested metadata. If you issue a SELECT query on a workspace, Drill impersonates the user logged in to the client to access the requested data.
- SHOW SCHEMAS
- SHOW DATABASES
- SHOW TABLES
- CTAS
- SELECT
- CREATE VIEW
- DROP VIEW
- SHOW FILES. NOTETo successfully run the CTAS and CREATE VIEW commands, a user must have write permissions on the directory where the table or view will exist. Running these commands creates artifacts on the file system.