Enabling Kerberos Security for Zeppelin
Describes how to set the principal and keytab properties for the Zeppelin server and configure interpreters to enable Kerberos for your Zeppelin installation.
Setting the Principal and Keytab Properties
- Set the principal and keytab of the Zeppelin server. To do this, you must edit the
following properties in the
zeppelin-site.xml:zeppelin.server.kerberos.principalzeppelin.server.kerberos.keytab
<property> <name>zeppelin.server.kerberos.principal</name> <value>mapr/node1.cluster.com@NODE1</value> <description>principal for accessing kerberized hdfs</description> </property> <property> <name>zeppelin.server.kerberos.keytab</name> <value>/opt/mapr/conf/mapr.keytab</value> <description>keytab for accessing kerberized hdfs</description> </property> - Restart the Zeppelin
server:
maprcli node services -action restart -nodes $(hostname) -name zeppelin - Configure your interpreters to work in the Kerberized environment, as described in the following sections. Note that the Spark, HBase, and HPE Ezmeral Data Fabric Database Shell interpreters do not require additional configuration to work properly in a Kerberized environment.
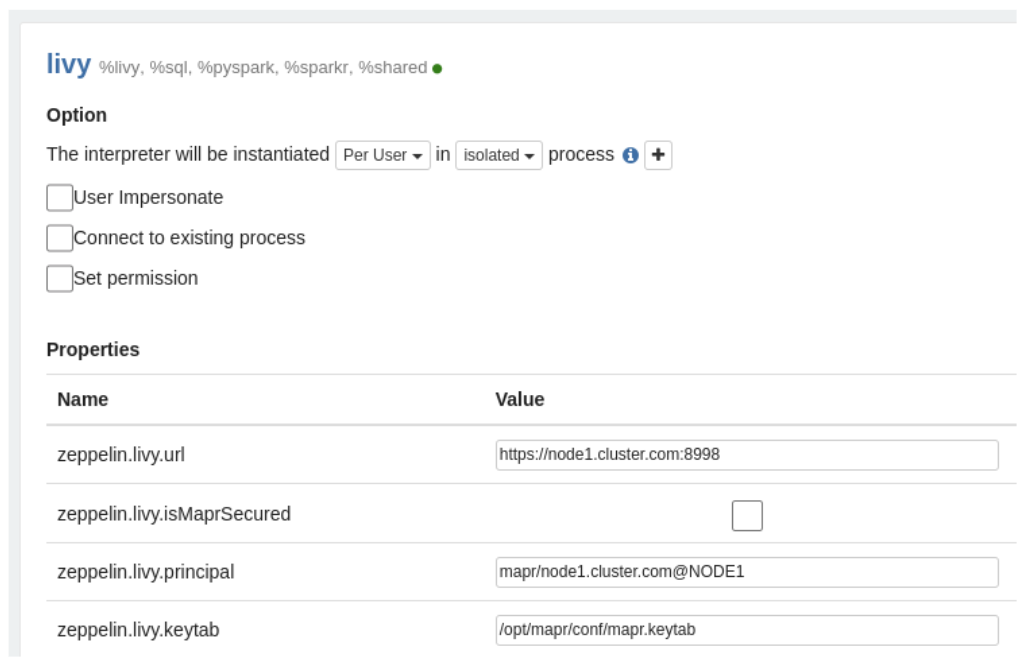
Configure the Livy Interpreter
To make the Livy interpreter work with the Livy server that is configured to use
Kerberos-based authentication, add the zeppelin.livy.principal and
zeppelin.livy.keytab options with corresponding values to the Livy
interpreter configuration:
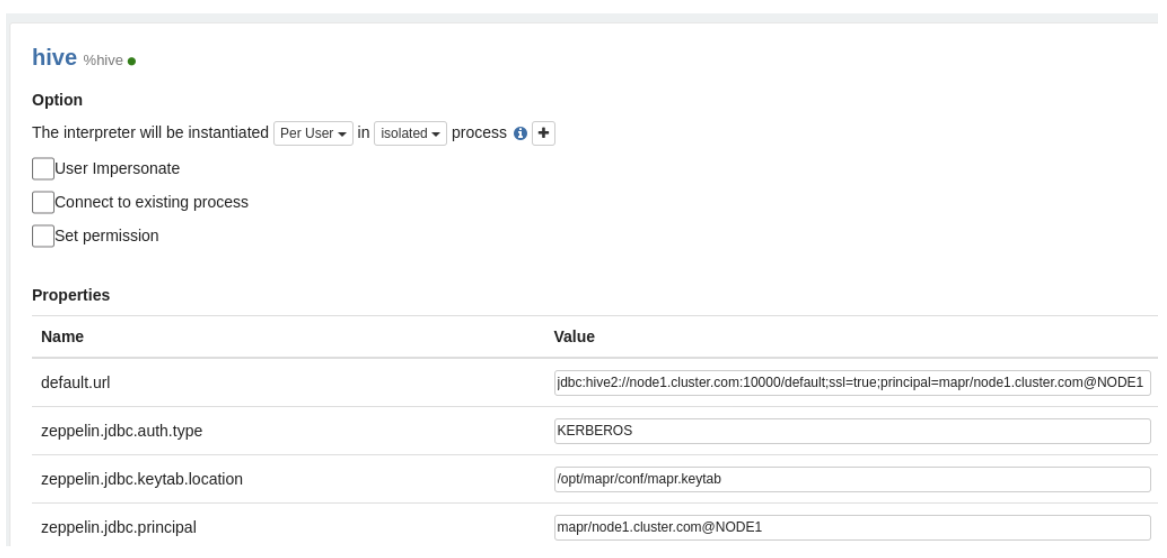
Configure the Hive Interpreter
To configure the Hive interpreter to work with the Kerberos-enabled HiveServer2, set the
the value of the principal option in the JDBC connection URL, and set
zeppelin.jdbc.auth.type, zeppelin.jdbc.principal and
zeppelin.jdbc.keytab.location properties in the Hive interpreter
configuration:
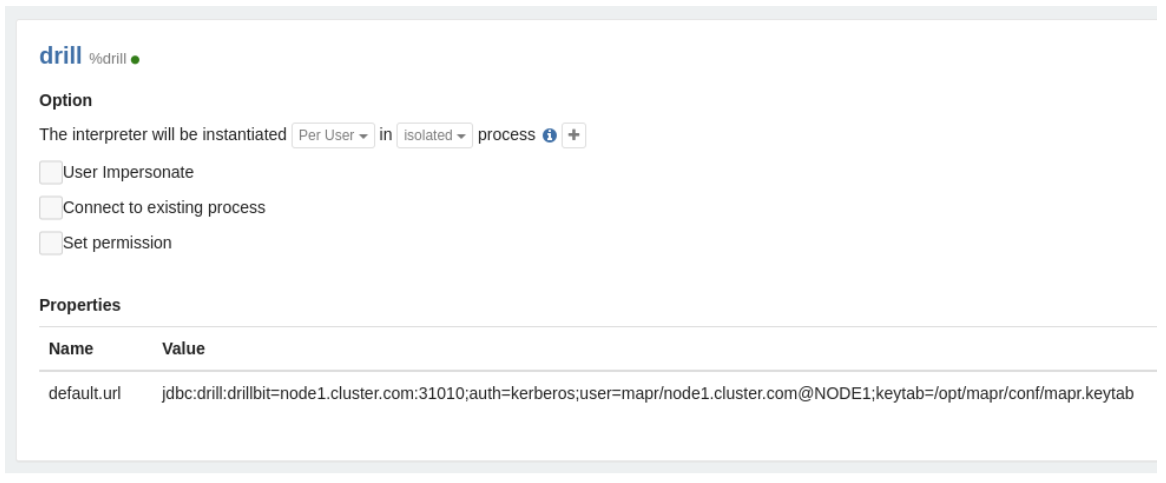
Configure the Drill Interpreter
To configure the Drill interpreter to work with Kerberos-enabled Drillbits, set the value
of the auth, user and keytab options in
the JDBC connection URL: