Networks and Subnets
HPE Ezmeral Runtime Enterprise hosts are connected through an external switch that is accessible to the network that your organization manages. Internally within HPE Ezmeral Runtime Enterprise, Kubernetes pods communicate through a private nonroutable virtual network that is not visible to the host network.
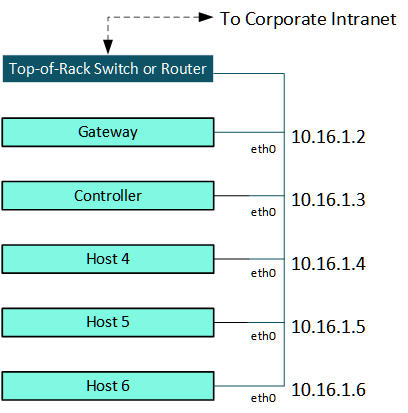
Routable Host Network
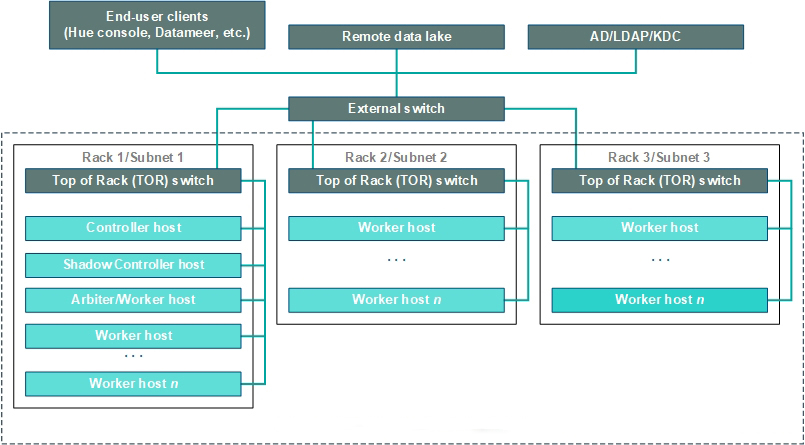
Hosts in a deployment of HPE Ezmeral Runtime Enterprise are typically deployed as one or more racks of servers that are connected to an external top-of-rack (ToR) switch. Each host (Controller, Shadow Controller, Arbiter, Gateway, and all Kubernetes hosts) has an IP address (such as 10.16.1.5) and an FQDN. This network must be both routable and part of the network that the IT department of your organization manages.
HPE Ezmeral Runtime Enterprise hosts can be deployed across multiple subnets, subject to certain requirements. See Multiple Subnets.
Private Nonroutable Pod Network
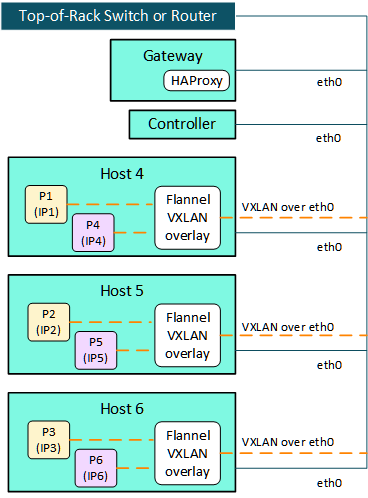
Kubernetes pods communicate with each other through an internal virtual network that is private (nonroutable) and managed by HPE Ezmeral Runtime Enterprise. This internal network is not accessible from the top-of-rack switch and is separate from the routable host network.
The virtual network for pods uses a VxLAN overlay. Canal, which combines Calico and Flannel, is used as the pod Network (CNI) Network Provider. This private, nonroutable pod network keeps the pod IP addresses hidden within the private network.
In Kubernetes, every container in a pod shares a network namespace, including the IP address and network ports. Kubernetes assigns an internal IP address to each pod, which appears in the following diagram as P1 (IP1), P2 (IP2), and so forth. Tenant network isolation is achieved by using Kubernetes Network Policies (link opens an external website in a new browser tab or window).
-
End-user access to services in the pods (such as Jupyter Notebook or web applications) is routed through a Gateway host that runs the HAProxy service.
-
Traffic that originates from pods is routed through the host network interface masquerading. Examples of traffic from pods includes accessing a remote HDFS, accessing enterprise systems such as Active Directory (AD), MIT KDC (Kerberos provider), SSO (Identity providers), and Certificate Authority (CA), and so forth.
Multiple Subnets
HPE Ezmeral Runtime Enterprise can be deployed across multiple subnets.
The use of multiple subnets is subject to the requirements described in Network Requirements.
The following diagram illustrates a sample deployment that uses multiple subnets.