Azure Architecture Notes
Describes architectural considerations for the HPE Ezmeral Data Fabric software-as-a-service (SaaS) platform when deployed on Microsoft Azure.
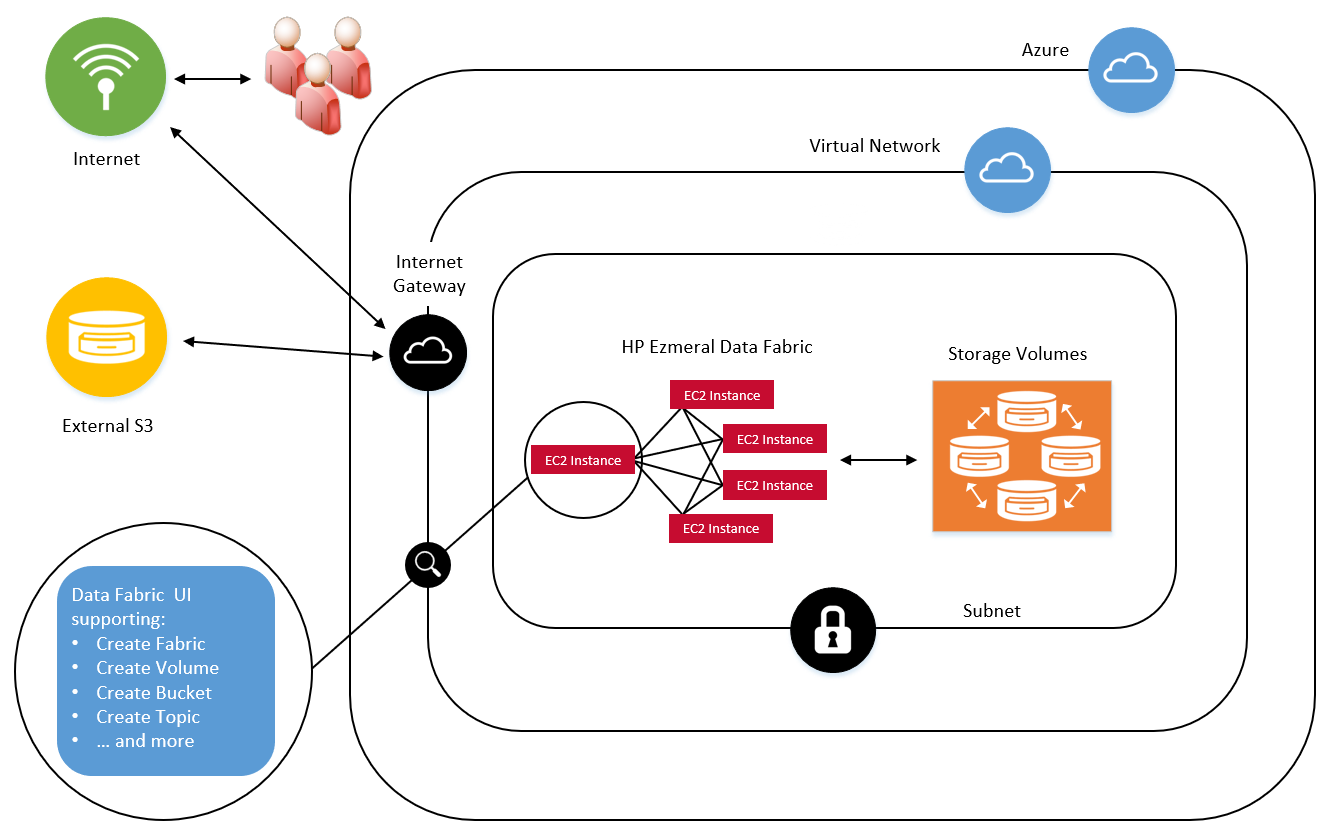
Deployment Topology
To take advantage of the benefits of cloud computing, you can provision an HPE Ezmeral Data Fabric in Microsoft Azure and in other public clouds. A single instance of the Data Fabric is referred to as a fabric. The fabric provides a high-performance file system for files, objects, tables, and streaming files and can be deployed quickly and easily. The HPE Ezmeral Data Fabric is designed so that many fabrics deployed in different public clouds or on premises can communicate with each other seamlessly in a global namespace (GNS).
Deployment Prerequisites
- Azure tenant ID
- Subscription ID
- Client ID
- Client secret
- Region
- Resource group name
- Virtual network
- Subnetwork
Public and Private Subnets
To enable a global namespace consisting of many fabrics accessible over the internet, the user must provide a public subnet. The global namespace cannot currently be implemented with private subnets. The Data Fabric architecture does not prevent the use of private subnets, but some code changes are required before private subnets can be supported. Note that air-gapped, on-premises installations are fully supported.
Regions and Availability Zones
- East US
- East US 2
- West US
- West US 2
Network Security Groups
During fabric creation, a network security group is created for each fabric. The network security group is configured with predefined in-bound and out-bound rules to support the list of ports required for fabric-to-fabric communication.
Instance, Disk, and Memory Information
Upgrades
When a new software version is available, the user is notified. At the user’s discretion, the platform can perform a non-disruptive, rolling upgrade from one major software version to another. However, upgrade capability is currently limited to on-premises deployments. See Upgrading a Data Fabric.
Scaling
Adding nodes to a fabric can be done using a rolling upgrade process. Note that adding nodes is currently supported only for on-premises deployments. See Adding Nodes (On-premises Deployment).
Administrative Interface
The Data Fabric UI provides a browser-based graphical user interface for monitoring and managing all fabrics in a global namespace.
SSO and Predefined Roles
The Data Fabric leverages the Keycloak identity and access management (IAM) solution to ensure that all the fabrics in a global namespace have access to the same user information. Keycloak can be used as a passthrough with other popular IAM solutions.
- Infrastructure Admin
- Fabric Manager
- Fabric User