Falco Container Runtime Security
The Falco Container Runtime Security feature of HPE Ezmeral Runtime Enterprise improves container security and threat detection.
Container Runtime Security
Falco container runtime security detects anomalies in the host and in containers by using the extended Berkeley Packet Filter (eBPF) to isolate kernel system calls. The feature is enabled by default and based on the Falco Open Source Software.
For more information about Falco, see the official Falco documentation.
Challenges, Features, and Benefits
- Vulnerability scanning (Shift Left) is good but not sufficient for many deployments.
- Never-ending CVE exploits and malicious intrusions are a fact of life.
- Microservices present a wider attack surface.
- Threats you do not see are impossible to deter.
- Runtime security by Falco that is enabled by default.
- Git-integrated automatic synchronization of new rules.
- Improved container security and threat detection.
- Reduced risk with immediate alerting.
- An early-warning system that leverages the most current detection rules for CVEs and malicious exploits.
Deploying Falco on an HPE Ezmeral Runtime Enterprise Kubernetes Cluster
Installing the Falco Kernel Module is optional.
If you choose to install Falco Kernel Modules see the following requirements and recommendations:
- The Falco Kernel Module you install on the host must be
the correct version for the host OS and OS version, must support Falco Kernel
Driver API Schema version 2.1.0, and must be installed using the Linux
modprobetool. See the official Falco documentation.When you use
modprobetool to install the module, themodinfotool can collect information about the module. For information aboutmodprobe, see themodprobe(8)manpage. - Hewlett Packard Enterprise recommends that you install the modules on all the hosts in a Kubernetes cluster.
- Hewlett Packard Enterprise recommends that you install the Falco Kernel module after you install the OS on the host, but before you install the HPE Ezmeral Runtime Enterprise software on that host.
-
If you install the Falco Kernel Modules on hosts before you add the hosts to HPE Ezmeral Runtime Enterprise, then HPE Ezmeral Runtime Enterprise automatically tags the hosts as
falco:true: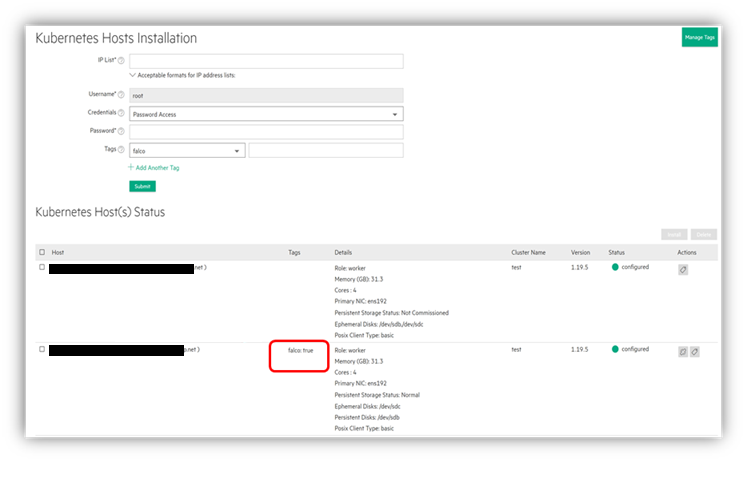
-
If you are installing the Falco Kernel Module on the hosts that are already in Kubernetes cluster, after you install the Falco Kernel Module on all the hosts in the cluster, you must manually add the
falco: truetag to each Kubernetes node in the cluster.
Enabling the Falcosidekick UI
The Falcosidekick UI enables you to view the latest events from Falco in real time through your web browser.
For information on the Falcosidekick UI, see this page from the Falco GitHub (link opens an external site in a new browser tab or window).
If you are using Kubernetes version 1.22 or higher, proceed as follows:
- To deploy the Falcosidekick UI, you must set up a storage class (PV/PVC) for
your Kubernetes cluster.
- If your Kubernetes cluster is configured with Data Fabric or has a
storage class marked as
default, the Falcosidekick UI uses the default storage class. - If your Kubernetes cluster does not have a default storage class defined, then HPE Ezmeral Runtime Enterprise is unable to deploy the Falcosidekick UI.
- If your Kubernetes cluster is configured with Data Fabric or has a
storage class marked as
- After setting up a storage class on your Kubernetes cluster, contact Hewlett Packard Enterprise support for assistance to manually
deploy the Falcosidekick UI.NOTEBeginning with Kubernetes version 1.22, you must use Falcosidekick UI version 2.2.5 or greater.
If you are using a version of Kubernetes lower than 1.22, proceed as follows:
- To enable the Falcosidekick UI for a Kubernetes cluster, enter the following
command:
kubectl patch svc falco-falcosidekick-ui --type='json' -p '[{"op":"replace","path":"/spec/type","value":"NodePort"}]' -n hpecp-falco - The annotation values that return tell you the gateway port you can use to
access the Falcosidekick UI.
For example:
!#to get gateway port kubectl describe svc falco-falcosidekick-ui -n hpecp-falco Name: falco-falcosidekick-ui Namespace: hpecp-falco ... Annotations: <example-gateway>/2802: m2-ess-vm77.<example.net>:10035 meta.helm.sh/release-name: falco ... Type: NodePort ... !#to access Falco UI: http://<example.net>:10035/ui
UEFI Secure Boot Limitation
If the Kubernetes node has UEFI Secure Boot enabled, any Falco-related functionality associated with the node will not be operational. For more information about UEFI Secure Boot, see What Is UEFI Secure Boot.