Importing an External Kubernetes Cluster
Importing an external Kubernetes cluster is not supported at this time. Kubernetes clusters must be created using HPE Ezmeral Runtime Enterprise.
HPE Ezmeral Runtime Enterprise provides a unified control plane to manage a fleet of Kubernetes clusters located both on-premises as well as those running in the managed cloud providers such as Elastic Kubernetes Service (EKS) in AWS. The dashboard allows you to monitor cluster health and usage statistics, and to provide Identity and Access Management across clusters.
Once an external cluster is imported and registered within the platform, you may then create tenants, set up Role Based Access Controls, deploy applications, and use many of the same features as a Kubernetes cluster created within HPE Ezmeral Runtime Enterprise. Importing external Kubernetes clusters is not supported in HPE Ezmeral Runtime Enterprise Essentials.
You can import clusters from:
- Microsoft Azure: See AKS.
- Amazon Elastic Kubernetes Service: See EKS.
- Google Kubernetes Engine: See GKE.
- Enterprise Pivotal Container Service: See PKS.
Be sure to also see Limitations at the bottom of this article for information on the limitations that apply to imported Kubernetes clusters compared to those created within HPE Ezmeral Runtime Enterprise.
Importing the Cluster
This section describes importing an existing Kubernetes cluster.
Requirements
The following requirements must be met in order to import an external Kubernetes cluster from EKS:
- The external Kubernetes cluster must already exist before you begin the import process. Please refer to your provider's documentation for instructions.
- The cloud-based Kubernetes clusters requires a private endpoint, and all of the pods in this cluster must be able to access the HPE Ezmeral Runtime Enterprise control plane.
- A bidirectional VPN must be configured to allow communications between HPE Ezmeral Runtime Enterprise and the external Kubernetes cluster, if applicable. Please refer to your provider's documentation for instructions.
- Domain name resolution must be configured so that the pods launched on the external cluster can resolve the hostnames of the HPE Ezmeral Runtime Enterprise control plane. This can be achieved in multiple ways. Please refer to the Kubernetes documentation and your provider's documentation for instructions (links open external websites in new browser tabs/windows).
- The external Kubernetes cluster must be accessible using
kubectlto get the information needed to import that cluster. - The user accessing the external Kubernetes cluster must have privileges to create and elevate a service account.
- The external Kubernetes cluster must include a service account with a cluster-admin role binding. See Step One: Create the Service Account, below.
- A Default StorageClass must already be set up for the external Kubernetes Cluster. Please refer to your cloud provider documentation for instructions.
Step 1: Gather Necessary Information
Execute the following commands on any host that can access the external
Kubernetes cluster using a kubeconfig received by following
your cloud provider's instructions.
- Create a service account by executing the command below. You can choose any
namespace for the account as long as the rest of the commands also specify the
same namespace. This example uses the default namespace.
kubectl create serviceaccount abc123 - Assign the
cluster-adminrole binding for the newly created service account. The default in the following command is the namespace where the service account was created.kubectl create clusterrolebinding add-on-cluster-admin --clusterrole=cluster-admin --serviceaccount=default:abc123 - Obtain the CA certificate and bearer token data by executing the following
commands. You will provide the contents of the token.base64 and ca.crt.base64
files to the HPE Ezmeral Runtime Enterprise web interface when importing the cluster.
SA_TOKEN=`kubectl get serviceaccount/abc123 -o jsonpath={.secrets[0].name}` kubectl get secret $SA_TOKEN -o jsonpath={.data.token} > token.base64 kubectl get secret $SA_TOKEN -o jsonpath={'.data.ca\.crt'} > ca.crt.base64 - The pod DNS domain name is generally set to
cluster.localby default on all external clusters. If you are unsure, then execute the following command to check the DNS Corefile:
kubectl describe configmaps/coredns -n kube-systemStep Two: Import the Cluster
To import an external Kubernetes cluster:
-
Click the Import Kubernetes Cluster button in the Kubernetes Clusters screen.
The Step 1: Import Configurations screen appears.
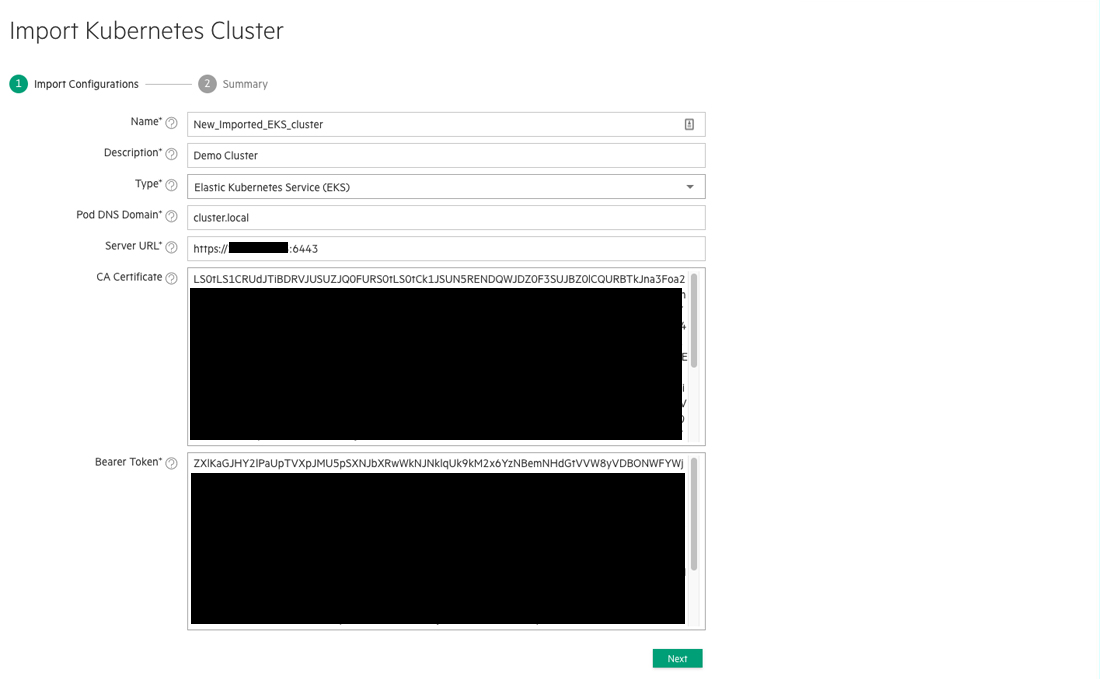
- Enter the following information in the appropriate fields:
- Name: Provide a name for the external Kubernetes cluster that you are importing.
- Description: Enter a brief description for this cluster.
- Type: Use this pull-down menu to select Generic, AKS, EKS, GKE, or PKS, as appropriate.
- Pod DNS Domain: Enter the FQDN of the pods in the imported cluster.
- Server URL: Enter the complete URL to the server that hosts the cluster, including the port number.
- CA Certificate: Paste the CA certificate that you received by executing the script in Step 1: Gather Necessary Information into this field.
- Bearer Token: Paste the bearer token that you received by executing the script in Step 1: Gather Necessary Information into this field.
-
Click Next.
The Step 2:Summary screen appears.

- Review the summary of cluster import parameters, and then either click Submit to finish importing the external Kubernetes cluster or click Previous to return to the Step 2: Application Configurations screen.
AKS
Please visit the following links for additional background information when importing an existing Kubernetes cluster from Microsoft Azure Kubernetes Service (AKS) (links open external websites in a new browser tab/window):
EKS
Please visit the following links for additional background information when importing an external Kubernetes cluster from EKS (links open external websites in a new browser tab/window):
GKE
Please visit the following links for additional background information when importing an existing Kubernetes cluster from Google Kubernetes Engine (GKE). Please visit the following links for additional background information (links open external websites in a new browser tab/window):
PKS
Please visit the following links for additional background information when importing an existing Kubernetes cluster from Enterprise Pivotal Container Service (PKS). Please visit the following link for additional background information (link opens an external website in a new browser tab/window):
PKS clusters are created inside your local environment. Thus:
- VPC and VPN are not required.
- DNS and default Storage Class are required.
Limitations
The following limitations apply to imported Kubernetes clusters:
- The Kubernetes Cluster Details screen does not display the Services and Alerts tabs.
- FS mounts are not available. A member of a tenant in an imported cluster therefore cannot use the Kubectl tab of the Kubernetes Applications screen to apply YAML or JSON files from a shared filesystem. See The Kubernetes Applications Screen.
- HPE Ezmeral Runtime Enterprise does not manage the lifecycle (expanding, shrinking, upgrading, or deleting) of the external Kubernetes cluster. You must make these changes using the provider's console.
- Deleting an imported Kubernetes cluster only unregisters it from HPE Ezmeral Runtime Enterprise; it does not delete the cluster from the provider.
