OPA Gatekeeper Policy Configuration
Describes configuration of policies using Open Policy Agent (OPA) Gatekeeper, a Rego-based policy engine implemented in HPE Ezmeral Runtime Enterprise as an admission controller for Kubernetes clusters.
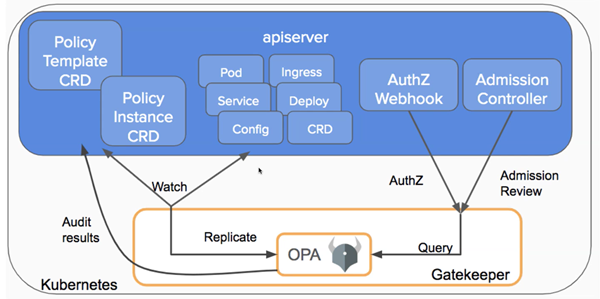
HPE Ezmeral Runtime Enterprise leverages OPA Gatekeeper as an admission controller to validate and enforce policies on the cluster. OPA Gatekeeper is installed as a mandatory system add-on, which is automatically created for HPE Ezmeral Runtime Enterprise users. For more information about OPA Gatekeeper, see the official OPA Gatekeeper documentation (link opens an external website in a new browser tab or window).
This feature is not available in HPE Ezmeral Runtime Enterprise Essentials.
You can use Centralized Policy Management to define and manage OPA Gatekeeper policies stored in a Git repository, and apply them to clusters managed by HPE Ezmeral Runtime Enterprise. For information, see Centralized Policy Management.
Default OPA Policies for Kubernetes Clusters
kubectl get constraints command to list all default
policies.The following default policies are configured as dry run:
psp-non-root-user-and-grouppsp-host-network-portspsp-host-filesystem
-
The
psp-privileged-containerpolicy ensures that privileged workloads run only in reserved (system) namespaces.k8spspprivilegedcontainer.constraints.gatekeeper.sh/psp-privileged-container -
The
psp-non-root-user-and-grouppolicy ensures pods with nonroot user and group run only in reserved (system) namespaces.k8spspnonrootuserandgroup.constraints.gatekeeper.sh/psp-non-root-user-and-group -
The
psp-host-network-portspolicy ensures pods that use host network and host port run only in reserved (system) namespaces.k8spsphostnetworkingports.constraints.gatekeeper.sh/psp-host-network-ports -
The
psp-host-filesystempolicy ensures pods that use host file system run only in reserved (system) namespaces.k8spsphostfilesystem.constraints.gatekeeper.sh/psp-host-filesystem
Creating OPA Policies
Create OPA Gatekeeper policies with Rego policy language, as described in Rego Policy Language.
For information and tutorials on using OPA Gatekeeper with Kubernetes, see the official OPA Gatekeeper documentation (link opens an external website in a new browser tab or window).
Applying, Modifying, and Deleting OPA Policies
Apply, modify, and delete OPA Gatekeeper policies, including default policies, as follows:
-
After you have created a policy with Rego, apply the constraint and template objects on a Kubernetes cluster as follows. On the Kubernetes master node enter the commands:
kubectl apply -f constraint_template.yamlkubectl apply -f constraint.yaml -
To modify a policy, update the constraint object associated with the policy with the following command:
kubectl edit constraint.yaml - To delete a policy, use the following
command:
kubectl delete constraint.yaml
