Editing an Existing DataTap
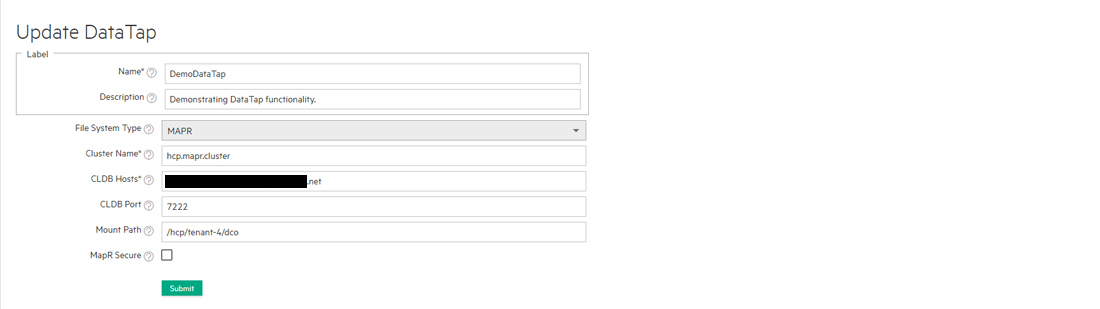
Tenant Administrators have the ability to edit DataTaps. In the DataTaps screen, clicking the Edit icon (pencil) in the Actions column of the table opens the Update DataTap screen for the selected DataTap.
Please see About DataTaps for important limitations on the directories that a DataTap can point to.
To edit a DataTap, you may modify some or all of the following:
- Name: Rename the DataTap by entering a new name in the Name field. This name may contain letters (A-Z or a-z), digits (0-9), and hyphens (-), but may not contain spaces.
- Description: Update the description of the DataTap by providing a new description in the Description field.
- Select the storage device type using the Select Type pull-down menu.
- MAPR: See MAPR Parameters, below.
- HDFS: See HDFS Parameters, below.
- NFS:See NFS Parameters, below. NFS is not available for Kubernetes tenants.
When you have finished modifying the parameters for the DataTap, click Submit to modify that DataTap.
Editing a DataTap that is being used by a currently running job can cause file access errors within that job.
MAPR Parameters
If you selected MAPR as the DataTap type, then enter the following parameters::
- Cluster Name: Name of the MapR cluster. See the MapR articles Creating the Cluster and Creating a Volume articles.
- CLDB Hosts: DNS name or address of the container location database of a MapR cluster. See the MapR article Viewing CLDB Information.
- Port: Port for the CLDB server used to access the MapR file system. See the MapR article Specifying Ports.
- Mount Path: Complete path to the directory containing the data within the specified MapR file system. You can leave this field blank if you intend the DataTap to point at the root of the MapR cluster. See the MapR articles Viewing Volume Details and Creating a Volume.
- MapR Secure: Checking this check box if MapR cluster is secured. When the MapR cluster is secured, all network connections require authentication, and all moving data is protected with wire-level encryption. MapR allows applying direct security protection for data as it comes into and out of the platform without requiring an external security manager server or a particular security plug-in for each ecosystem component. The security semantics are applied automatically on data being retrieved or stored by any ecosystem component, application, or users. See the MapR article Security.
- Ticket: Enter the complete path to the MapR ticket. MapR uses tickets for authentication. Tickets contain keys that are used to authenticate users and MapR servers. In addition, certificates are used to implement server authentication. Every user who wants to access a secure cluster must have a MapR ticket. Tickets are encrypted to protect their contents. See the MapR articles Tickets and How Tickets Work.
- Ticket Type: Select the ticket type. This will be one of the
following:
- User: Grants access to individual users with no impersonation support. The ticket UID is used as the identity of the entity using this ticket.
- Service: Accesses services running on client nodes with no impersonation support. The ticket UID is used as the identity of the entity using this ticket.
- Service
(with impersonation): Accesses services running on client nodes
to run jobs on behalf of any user. The ticket cannot be used to
impersonate the
rootormaprusers. - Tenant: Allows tenant users to access tenant volumes in a multi-tenant environment. The ticket can impersonate any user.
- Ticket User: Username to be included in the ticket for authentication.
- MapR Tenant Volume: Indicates whether or not the mount path is a MapR tenant volume. See the MapR article Setting Up a Tenant.
- Enable Impersonation: Enable user impersonation.
HDFS Parameters
If you selected HDFS as the DataTap type, then enter the following parameters:
- Host: Enter either the hostname or IP address of the HDFS NameNode in the Host field.
- Standby NameNode Host: Enter the hostname or IP address of the HDFS standby NameNode, if any, in the Standby NameNode Host field.
- Port: Enter the NameNode port number in the Port field. Leave blank to use the default HDFS NameNode port.
- Path: Enter the HDFS directory under the share to use for the DataTap in the Path field. You may also click the Browse button to open an explorer window to navigate to the desired directory. You can leave this field blank if you intend the DataTap to point the root of the specified file system.
- Kerberos Protection: You can enable or disable Kerberos protection for the selected DataTap by checking or clearing the Kerberos Protected check box, as appropriate. See HDFS DataTap Kerberos Security.
- Username: If needed, you can enter a valid username for accessing the HDFS.
NFS Parameters
If you selected NFS as the DataTap type, then enter the following parameters:
- Host: Enter either the hostname or IP address of the file system host in the Host field.
- Share: Enter the name of the share in the Share field.
- Path: This field specifies where the top of the DataTap's file system is rooted. For manually created DataTaps, this field must either be empty, or it must point to an existing subdirectory of the indicated storage system. For an automatically created tenant default DataTap, then HPE Ezmeral Runtime Enterprise will automatically create the indicated subdirectory if necessary, whenever any writes are done to that DataTap. Either enter the directory under the share to use for the DataTap in the Path field (click the Browse button to open an explorer window to navigate to the desired directory, if desired), or leave this field blank to point the DataTap to point the root of the specified share.
Also, be sure to configure the storage device to allow access from each host and each Controller and Worker that will using this DataTap.